What you will need
Writing to USB
First, you'll need to find your managed Chromebook's board name. This can be done by going to chrome://version on your Chromebook and copying the word after "stable-channel", or with a variety of other methods.
If your board name is in the list below, your board has a publicly leaked RMA shim. If it's not, you'll have to source it on your own... somehow.
brask, brya, clapper, coral, dedede, enguarde, glimmer, grunt, hana, hatch, jacuzzi, kukui, nami, octopus, orco, pyro, reks, sentry, stout, strongbad, tidus, ultima, volteer, zork
First you need to download a sh1mmer bin. Download a shim at files.ultimatesrv.com
, and build it with the sh1mmer web builder
Once you've obtained a MODIFIED SHIM (NOT A RAW SHIM), you can continue.
Download the
Chromebook Recovery Utility extension
Once the downloads are complete, launch the recovery utility and plug your USB into your personal computer. Note that your USB will be completely cleared and partitioned.
In the recovery utility window, click the settings icon and press "use local image".
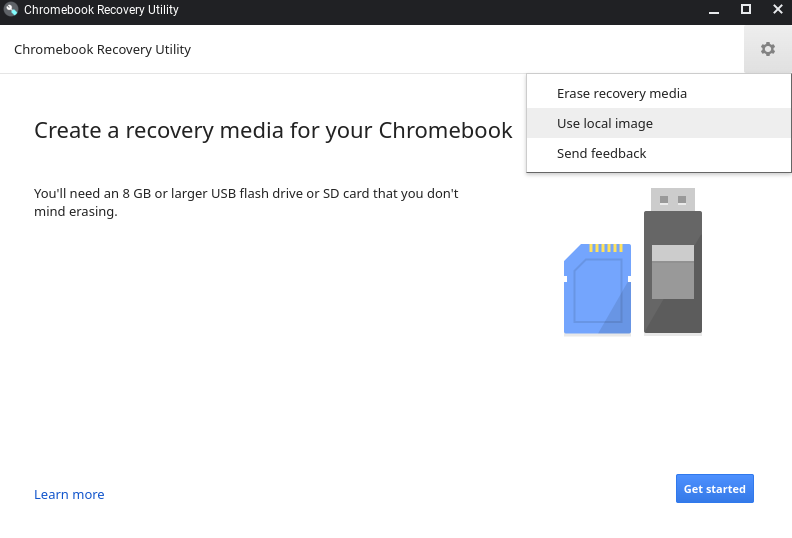
Select your shim file, identify your USB, and start the writing process. This will take about 10 minutes.
Executing on Chromebook
Once writing is complete, enter recovery mode on your Chromebook. This is done by pressing the power button, reload key (↻), and esc key at the same time. Your screen should look one of the images below:
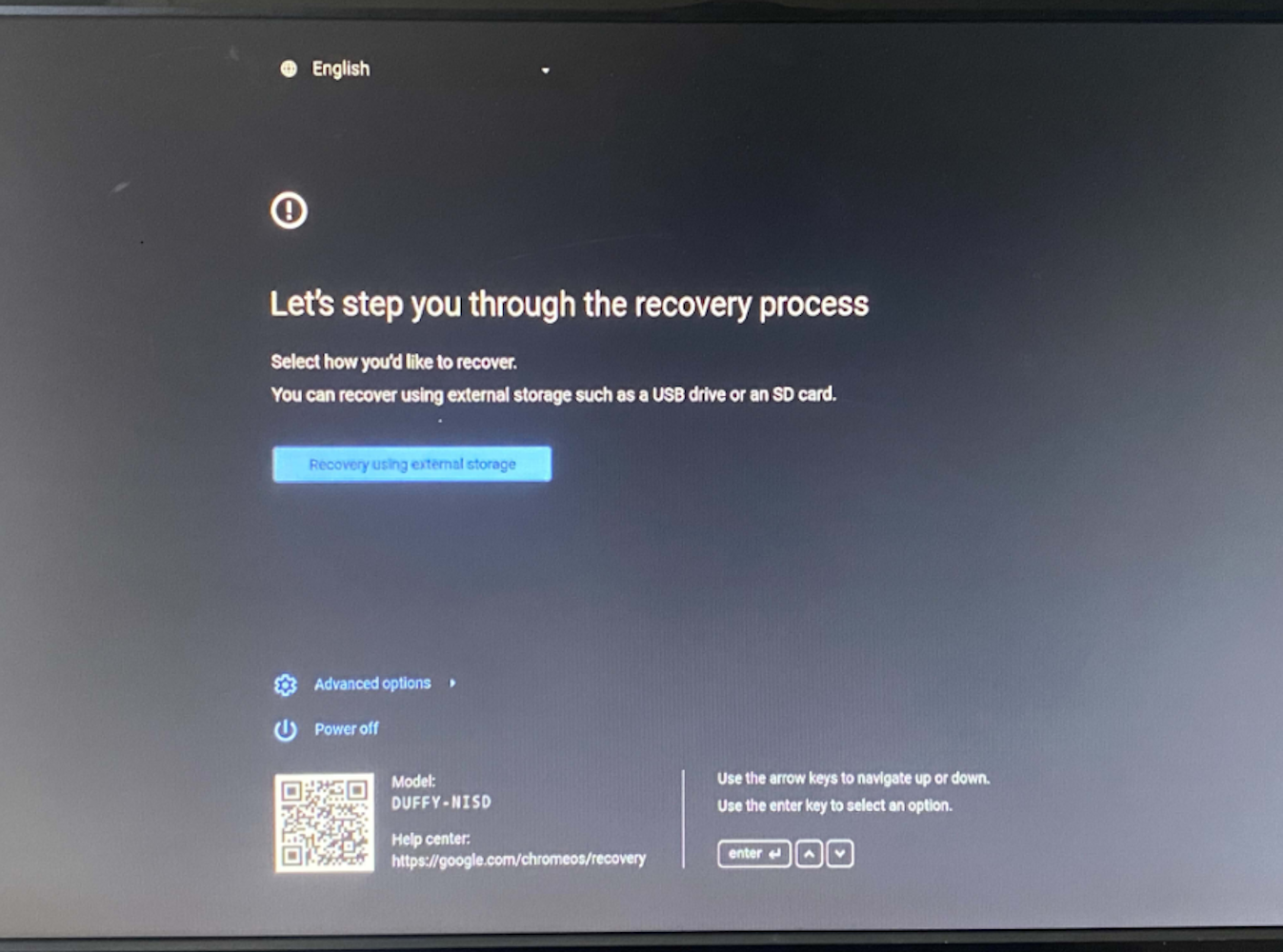
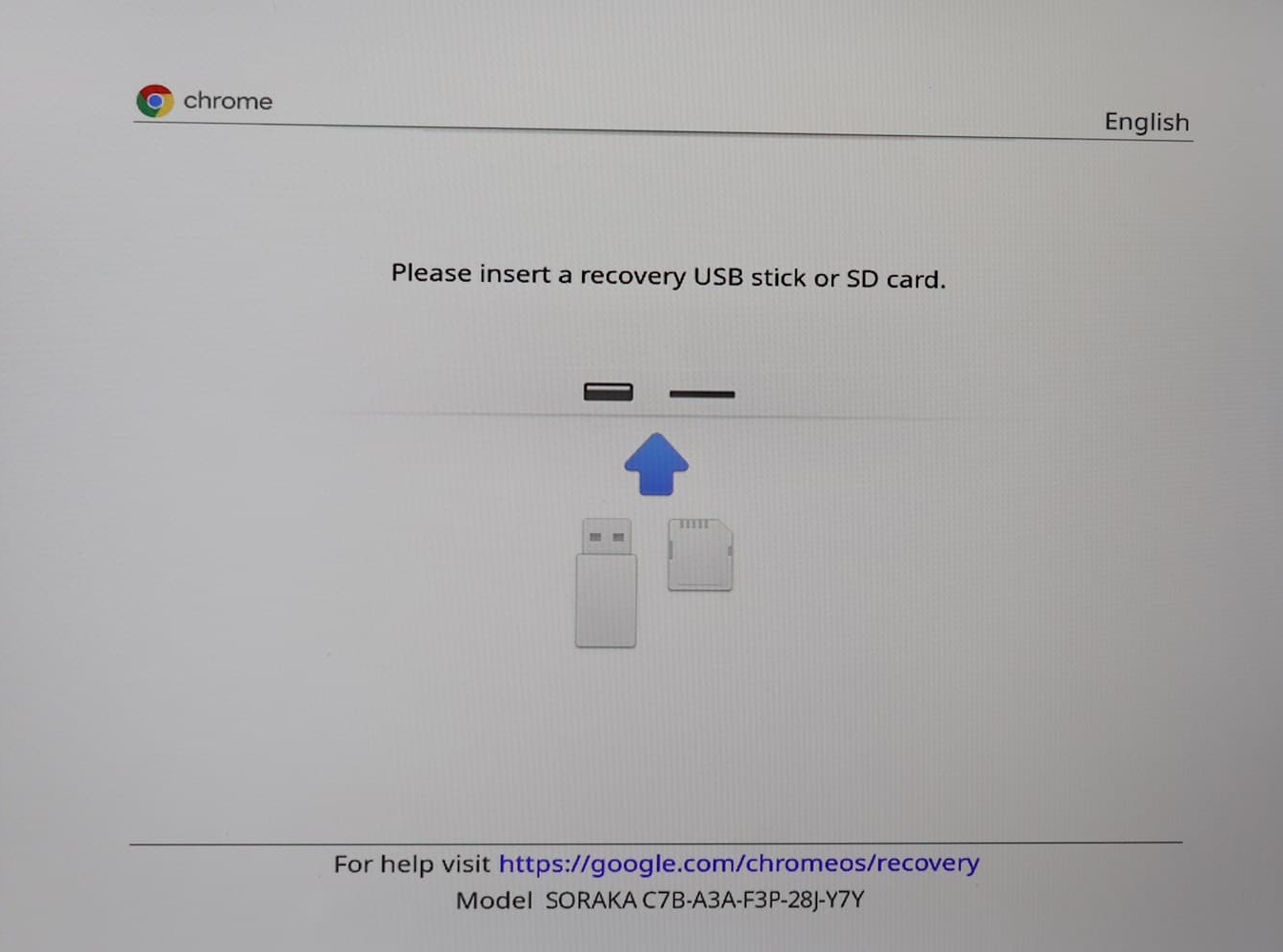
Press ctrl+d on this screen, then press enter.
It will now say something about "returning to secure mode" or that "OS verification is off". You will most likely not actually be in dev mode, but the exploit will work regardless. Your screen should look like one of the images below:
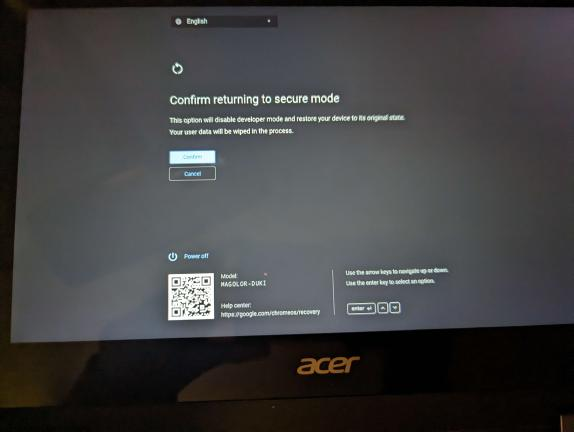
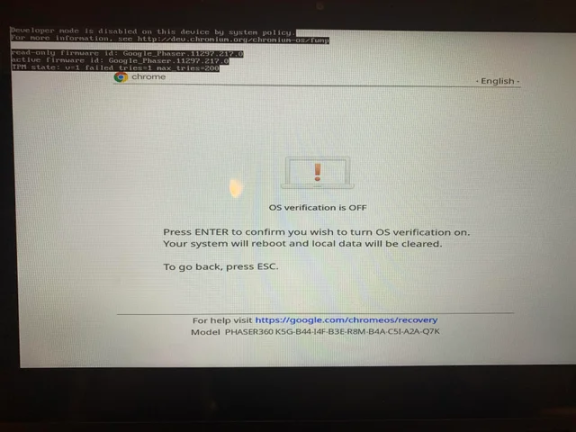
On this screen, press the power button, reload key (↻), and esc key at the same time again! This is very important and cannot be skipped.
Once it re-shows the original recovery screen, plug your shimmed USB into your Chromebook, and press the power button, reload key (↻), and esc key again. After a brief black-and-white loading screen, you should be in the SH1MMER menu.
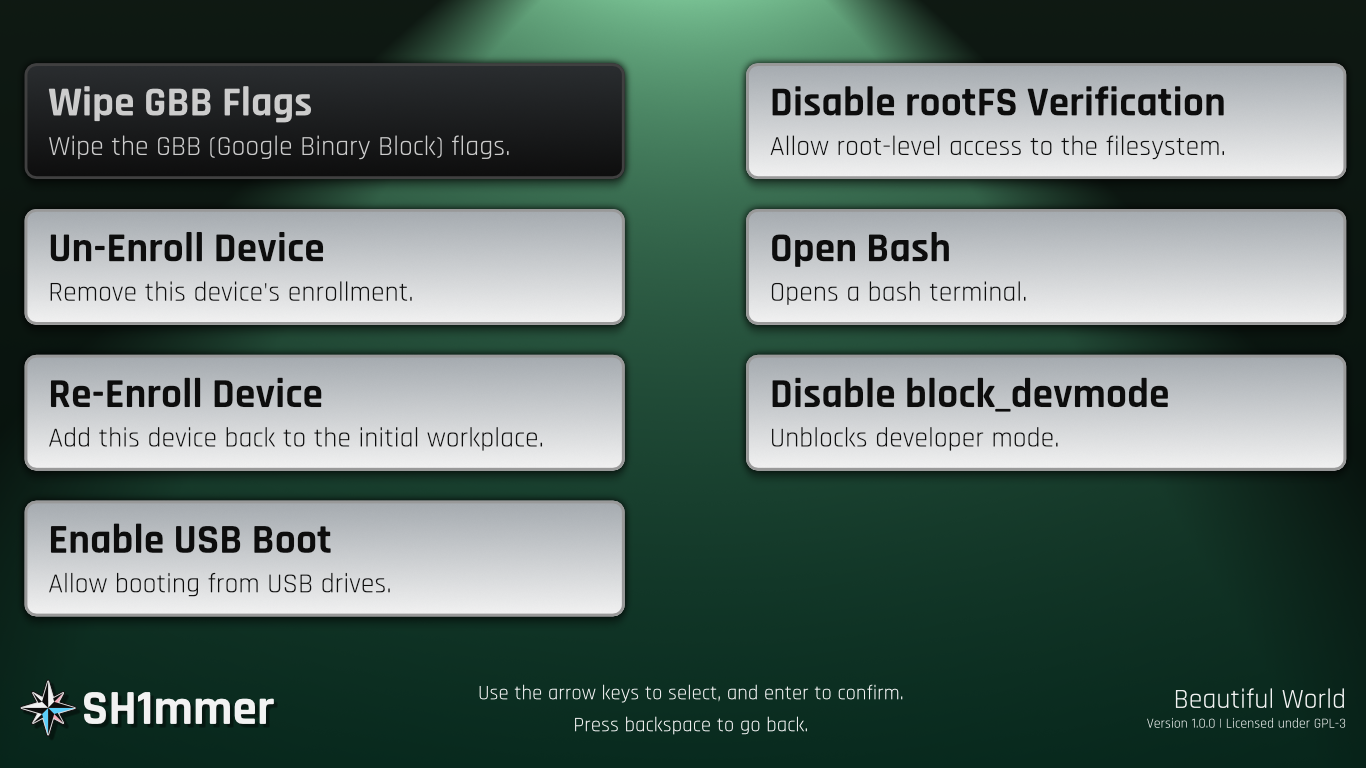
Play around with the UI, exit, and reboot.
What now?
You will now be able to, among other things, unenroll your Chromebook. It will now behave entirely as if it is a personal computer and no longer contain spyware or blocker extensions. After you do this and get past the "determining device configuration" screen, you will be able to actually turn dev mode on.
Note that while unenrolled, it is recommended to add your personal account first, then add your school account, then switch between the two as needed. Mercury Workshop does not condone the use of SH1MMER or unenrolling to cheat in school.
The biggest challenges with unenrolling are connecting to the school network and taking state or national exams (since there are no kiosk apps anymore).
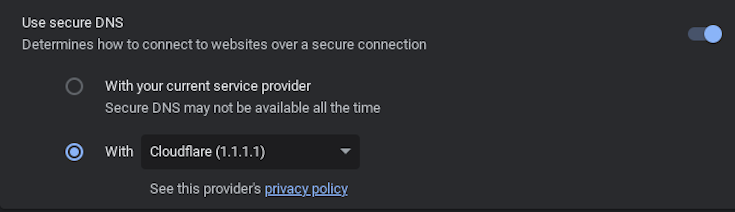
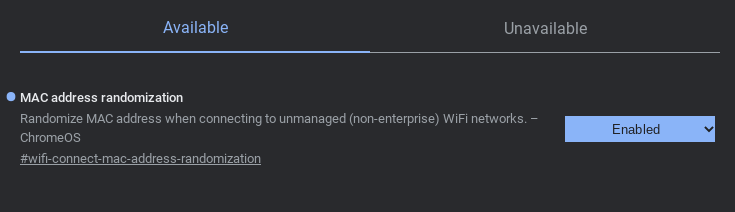
There are many methods to get a school Wi-Fi password while enrolled, including the policy netlog trick. While on a school account and unenrolled, you can bypass Wi-Fi blocks by using a secure DNS such as Cloudflare 1.1.1.1 from chrome://os-settings/osPrivacy. It is also recommended to enable "MAC Address Randomization" in chrome://flags to stay hidden.
To take a kiosk exam, the safest option is to re-enroll temporarily. Instructions for doing that are hosted at this TXT file. Saving a copy of this file for future reference is probably a smart move.